Browser Networking
- Browser
- Platform for fast, efficient and secure delivery of Web apps
- Many components
- parsing, layout, style calculation of HTML and CSS, JavaScript execution speed, rendering pipelines, and networking stack
- When network is slow, e.g. waiting for a resource to arrive
- all other steps are blocked
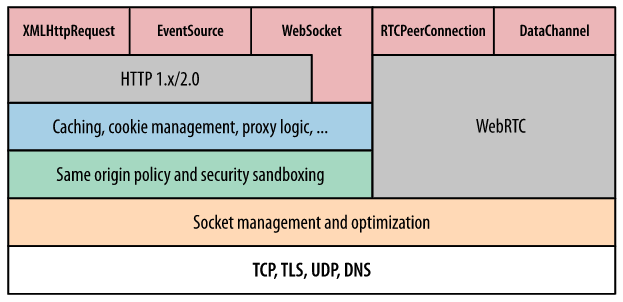
Connection Management
- Network socket management and optimization
- Socket reuse
- Request prioritization
- Protocol negotiation
- Enfocring connection limits
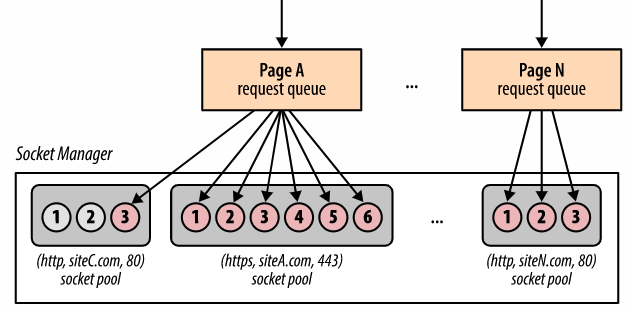
- Socket manager
- Sockets organized in pools (connection limits and security constraints)
- origin = (protocol, domain, port number)
Network Security
- No raw socket access for app code
- Prevents apps from initiating any connection to host
- For example port scan, connect to mail server, etc.
- Network security
- Connection limits
- protect both client and server from resource exhaustion
- Request formatting and response processing
- Enforcing well-formed protocol semantics of outgoing requests
- Response decoding to protect user from malicious servers
- TLS negotiation
- TLS handshake and verification checks on certificates
- User is warned when verification fials, e.g. self-signed cert is used
- Same-origin policy
- Constraints on requests to be initiated and to which origin
Mashups
- Web application hybrid
- App uses APIs of two or more applications
- Types
- Data mashup – integration/aggregation of data (read only)
- Service mashup – more sophisticated workflows (read, write)
- Visualization – involves UI
- For example, third-party data displayed on the Google map
- Client-Server View
- client-side mashups (in a browser)
- JavaScript, Dynamic HTML, AJAX, JSON/JSONP
- server-side mashups
- server-side integration of services and data
- Any language
XMLHttpRequest (XHR)
- Interface to utilize HTTP protocol in JavaScript
- standardized by at W3C
- basis for AJAX
- Asynchronous JavaScript and XML
- Typical usage
- Browser loads a page that includes a script
- User clicks on a HTML element
- it triggers a JavaScript function
- The function invokes a service through XHR
- same origin policy, cross-origin resource sharing
- The function receives data and modifies HTML in the page
XHR Interface – Key Methods and Properties
- Method and properties of XHR object
open, opens the request, parameters:
method– method to be used (e.g. GET, PUT, POST),
url– url of the resource,
asynch– true to make asynchronous call,
user,pass– credentials for authentication.onReadyStateChange– JavaScript function object, it is called whenreadyStatechanges (uninitialized, loading, loaded, interactive, completed).send,abort– sends or aborts the request (for asynchronous calls)status,statusText– HTTP status code and a corresponding text.responseText,responseXML– response as text or as a DOM document (if possible).onload– event listener to support server push.- See , or for a complete reference.
How XHR works
Fetch API
- XHR is callback-based, Fetch is promise-based
- Interface to accessing requests and responses
- Provides global
fetchmethod to fetch resources asynchronously - Can be easilly used in service workers
- Supports CORS and other extensions to HTTP
- Interfaces
Request– represents a request to be madeResponse– represents a response to a requestHeaders– represents response/request headers- Basic usage:
async function logMovies() {
const response = await fetch("http://example.com/movies.json");
const movies = await response.json();
console.log(movies);
}
Making request
- A
fetchfunction is available in globalwindow - It takes
pathand returnsPromise
fetch('https://api.github.com/users/tomvit')
.then(response => response.json())
.then(data => console.log(data))
.catch(error => console.error('Error:', error));
no-cors request- With Fetch, the request will be handled as with putting
srctoimg
fetch('https://google.com', {
mode: 'no-cors',
}).then(function (response) {
console.log(response.type);
});
- With XHR, the whole
responseTextwould be loaded into memory. - With Fetch, you can read chunks of response and cancel the stream when needed.