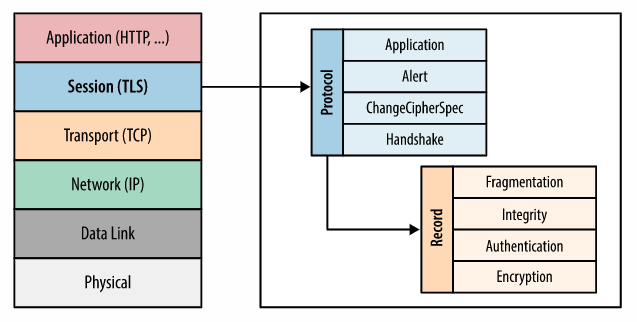
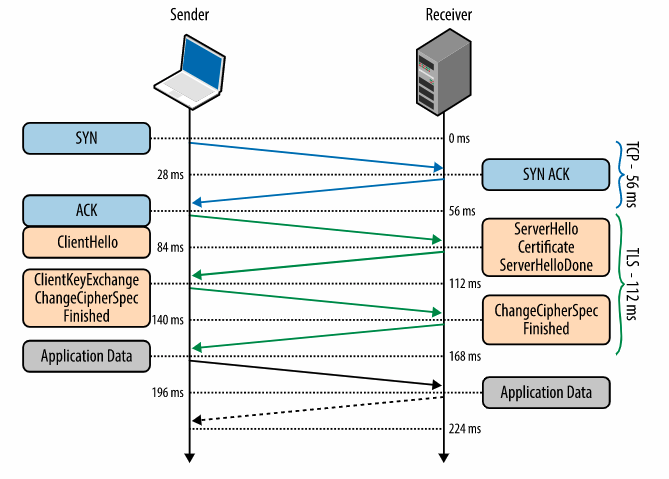
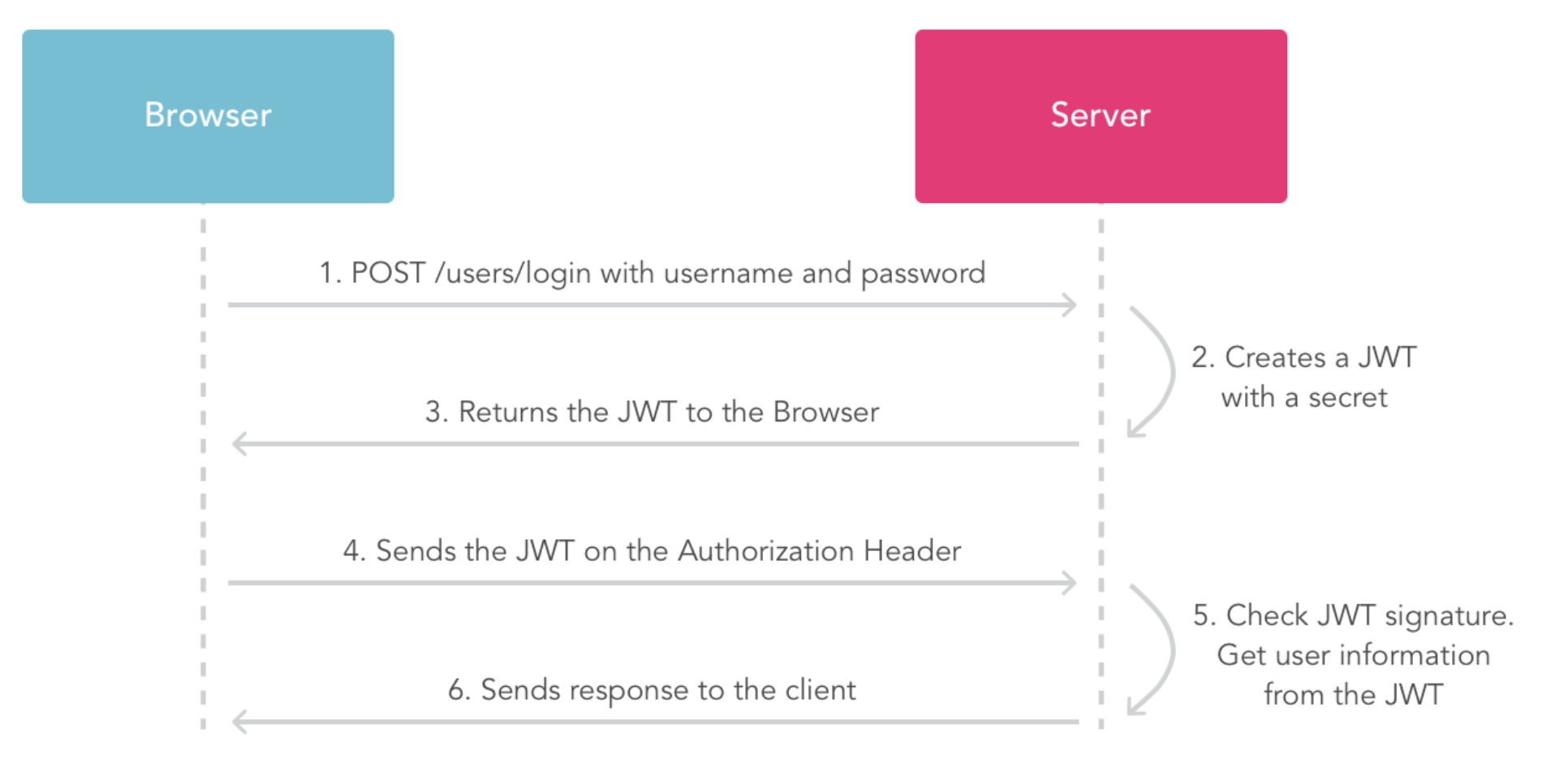
Callback + Access Token Request – steps 4, 5
- Callback
- authorization server calls back
redirect_uri
- client gets the
code and requests access_token
- example (resource owner grants access):
http://w20.vitvar.com/examples/oauth/callback.html?code=4/P7...
- when user rejects → same as client-side access
- Access token request
POST request to token endpoint
→ example Google token endpoint:
https://accounts.google.com/o/oauth2/token
POST /o/oauth2/token HTTP/1.1
Host: accounts.google.com
Content-Type: application/x-www-form-urlencoded
code=4/P7q7W91a-oMsCeLvIaQm6bTrgtp6&
client_id=621535099260.apps.googleusercontent.com&
client_secret=XTHhXh1S2UggvyWGwDk1EjXB&
redirect_uri=http://w20.vitvar.com/examples/oauth/callback.html&
grant_type=authorization_code
Access Token (cont.)
- Access token response
- Token endpoint responds with
access_token and refresh_token
{ "access_token" : "1/fFAGRNJru1FTz70BzhT3Zg",
"expires_in" : 3920,
"refresh_token" : "1/6BMfW9j53gdGImsixUH6kU5RsR4zwI9lUVX-tqf8JXQ" }
Refreshing a token
POST request to the token endpoint with grant_type=refresh_token
and
the previously obtained value of refresh_token
POST /o/oauth2/token HTTP/1.1
Host: accounts.google.com
Content-Type: application/x-www-form-urlencoded
client_id=21302922996.apps.googleusercontent.com&
client_secret=XTHhXh1SlUNgvyWGwDk1EjXB&
refresh_token=1/6BMfW9j53gdGImsixUH6kU5RsR4zwI9lUVX-tqf8JXQ&
grant_type=refresh_token
Accessing a resource is the same as in the client-side app